Who needs a rocket launcher when you have a keyboard?
The Morris Worm
Starting off this amazing hack-list, we travel back to 1988. Robert Tappan Morris creates a worm dubbed “Morris Worm.” This is no ordinary worm. In fact, Robert Morris has built the very first computer worm and transmits it through the Internet. At the time, Morris was a student attending the U.S. Cornell University.
While his research was not intended for malicious practices, but to merely determine the range of cyberspace, the infection was still launched. His worm was working perfectly until it hit a critical error and started to transform into a more malicious code. This worm then infected other computers and ultimately, performed probably one of the first ever denial service attacks. As a result, this worm infected 6,000 computers, costing around $10-$100 million just in repairs alone. This simple attack can easily be labeled as an unfortunate accident, but it was also the dawn of DDoS attacks, in which we see today.
“MafiaBoy” Michael Calce
Time warp to 2000 for another 15-year-old creating online mischief. Known in the real world as Michael Calce, he took the online alias “MafiaBoy.” Michael was dubbed as “the bratty kid who took down the Internet.”
Calce was a Canadian high school student when he contemplated unleashing a massive DDoS attack against several websites. But these weren’t just any websites; he attacked high-profile commercial companies including Amazon, CNN, eBay and Yahoo. The security researchers that had been assigned the case had estimated damages nearing $1.2 billion USD. Calce was still a juvenile, however, with a sentence of 8 months in open custody handed down in 2001. Calce was permitted Internet access, but it was restricted and monitored.
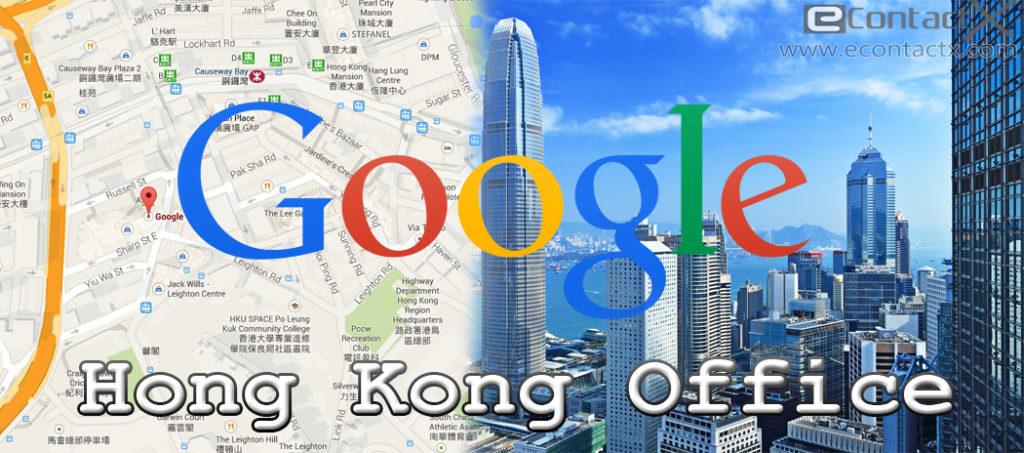
Google’s Chinese Security Breach
Fast forward to 2009, for Google’s Chinese-based headquarters detecting a security breach just before Christmas. This security breach opened a can of worms, implicating the Chinese Government. The hacktivists behind this attack accessed several of Google’s corporate servers, even more so, they also stole intellectual property.
A Google blog post had stated that they had “evidence to suggest that a primary goal of the attackers was to access the Gmail account of Chinese human rights activists.” After some extra digging, the security researchers had discovered several Gmail users based in the United States, China and Europe that had been routinely accessed without the original owner’s consent. Those targeted emails had then been cross referenced to those that supported the Human Rights in China. Naturally, since the Chinese government had been accused of flagrantly disregarding human rights, they became primary suspects for this investigation.
Google had placed their company into the Chinese market in 2006, using the domain
www.google.cn, capitulating it into a stringent Internet censorship regime. After the cyber attacks of 2009, Google moved their servers into Hong Kong to escape the Internet filtering policy.
Jonathan James and the DoD
It’s 1999, a time in which computer technology really started to boom. The United States Department of Defense, alongside with NASA, had been hacked by teenager, Jonathan James, 15.
James penetrated the secured computers hosted within the Department of Defense division and then proceeded to install a backdoor to their servers. James uploaded a virus onto the servers, allowing him to easily intercept digital emails being sent from different government sectors, with some emails containing usernames and passwords for various military computers.
Using some of the stolen information, he then proceeded to steal software made by NASA. This act ended up costing the space agency roughly $41,000 USD, and their systems shutdown for around 3 weeks. The NASA software was reported to be worth$1.7 million and supported a space station’s physical environment.
James was caught, yet, received a very light sentence due to his age and protected minor’s rights. However, sadly, James took his own life after being accused of assisting other hackers in stealing credit card information. In his suicide note he made it extremely clear that he was not associated with the theft of the credit card information.
Phreaking and Kevin Poulsen
Back in 1995, phreaking was making a huge spill everywhere. Kevin Poulsen aided the exposure to phone phreaking. Kevin is mostly famous for the hack into the Los Angeles phone system, in efforts of winning a new Porsche. The LA KIIS FM radio station was offering a reward of a Porsche 944 S2 for the 102nd caller, and Kevin wanted to guarantee his phone call’s success. In order to make sure that he would be the 102nd caller, Kevin just simply took over the phone network and blocked any and all calls going into the targeted radio station. As he was sure enough to win, he was also sentenced to a 5 year prison sentence for his crimes. Later on, Kevin became a senior IT editor for
Wired News.
Let’s DDoS the Church of Scientology
In more recent times, the Church of Scientology was hacked in January of 2008. A New Jersey teenager and a group of hackers who backed him up, launched a good size DDoS attack against the controversial church. This cyber-attack completely crippled the Scientology website, keeping it down for several days. Dmitriy Guzner, 19 at the time of the attack, received a prison sentence for his acts of cyber crime, and also a hefty fine of $250,000. However, fortunately for him, he was only in prison for 2 years and then, only had to pay the Church of Scientology $37,500.
The Solar Sunrise Attacks
The major crises of Solar Sunrise Technologies in 1998 was a systematic cyber attack launched directly against the United States, seizing well over 500 different government computer systems. Some of the compromised computers were also from private sectors. These hackers had exploited the computers that had been running on Sun Solaris operating systems – the reason why they were dubbed the “Solar Sunrise Attacks.”
The United States had assembled several different defense divisions, including aid from the FBI, as well as the Defense Information Systems Agency, in order to instigate a full investigation into this cyber attack. Surprisingly enough, this was not the act of any Iraqi cyber terrorist, but rather 3 teenagers from California. They were arrested and charged for the cyber crimes committed. This particular attack had highlighted just how efficient a well-coordinated cyber attack can ultimately cripple an entire country’s IT Infrastructure.
The Melissa Virus of 1999
Sometimes the simplest forms of malware can be the most expensive in damages, and the Melissa Virus from 1999 shows us just that.
This rather simple virus ended up costing over $80 million in damages. Infecting Microsoft’s Word documents and then automatically dismantling itself like an attachment from an email, it would then send out an email to the first 50 names hosted on the infected computer, provided that they had used Microsoft’s Outlook mail client. David Smith, the creator of Melissa, had no intentions of harming any computers with his virus, however, he was still sentenced to 20 months in prison. Oddly enough, the sales of antivirus software programs soared through the roof that year.
DDoS the Entire Internet, You Say?
Coming in at number 9, we land in 2002, when a cyber attack was directed towards all of the 13 domain name system’s main root servers, which were based in the United States. This cyber attack almost brought the entire Internet to its knees. Surprisingly enough, this attack was a rather simple, but complex, DDoS attack.
The entire operation lasted 1 hour and the amount of force behind the attack was the alarming feature. At that time in history, the United States Federal authorities had described it as the largest, and most complex, cyber attack seen. The Internet servers were severely strained for the entire hour, and it is reported that the users didn’t really notice any difference. However, if the attack had lasted even another 30 minutes, the entire Internet could have come to a complete standstill.
Gonzales’ Credit/Debit Hack – Largest in U.S. History
Finally, on our list of the top 10 most notorious cyber attacks, we find ourselves in 2009, when hackers have allegedly stolen tens of millions of credit card details. Gonzales, a hacker from Miami, Florida, was held responsible for one of the largest fraud cases in the history of the United States. Gonzales had stolen credit and debit card details from well over 250 different financial institutions. He was able to hack into the payment card network from various companies, such as the 7-Eleven store chain. Gonzales was faced with 3 different cases relating to the hacking charges, spreading out over three different states. Later, in December, Gonzales acknowledged his guilt.
This article (The 10 Most Notorious Hacks of All Time) is a free and open source. You have permission to republish this article under a Creative Commons license with attribution to the author and AnonHQ.